Use Cases
Building Confidential AI with TEE
Build confidential AI applications with Trusted Execution Environment technology.
Check Phala Network’s 2025 dAGI report to see how TEE is used in AI full stack.
Introduction
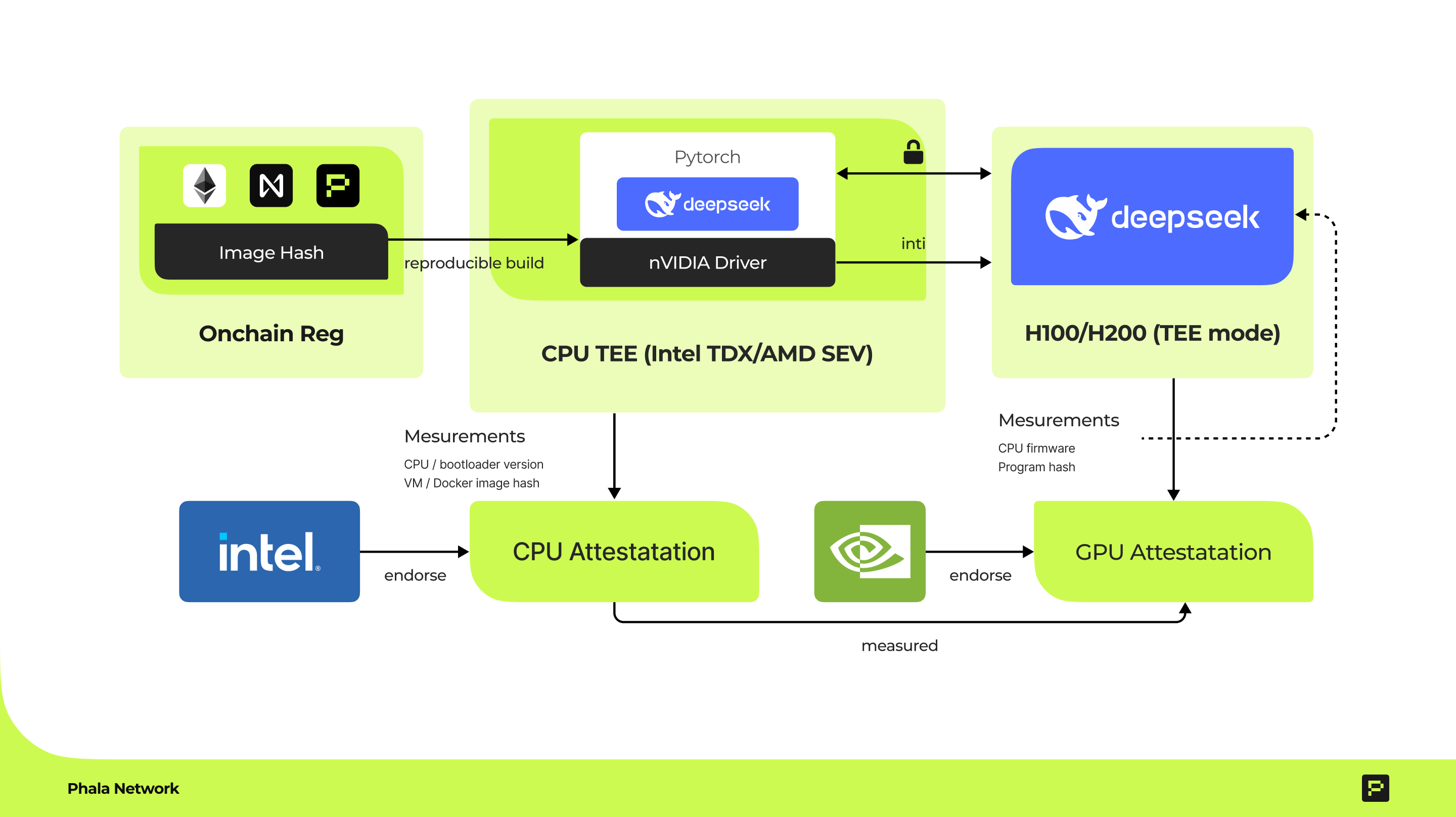
The Need for TEE in AI Systems
The integration of TEE technology with AI addresses several critical challenges:- Data Privacy Concerns: AI training and inference often require access to sensitive personal, financial, or proprietary data. TEEs ensure this data remains encrypted and protected even during processing.
- Model Protection: Valuable AI models represent significant intellectual property that needs protection from theft, tampering, or unauthorized access. TEEs can safeguard these assets throughout their lifecycle.
- Verifiable Computation: Users need assurance that AI computations are performed correctly and that results haven’t been manipulated. TEE attestation provides cryptographic proof of the execution environment’s integrity.
- Preventing Data Leakage: Even in systems designed for privacy, subtle information leakage can occur through side channels or model outputs. TEEs provide an additional layer of protection against such vulnerabilities.
Key Benefits of TEE for AI Applications
- Confidential AI Inference: Run inference on sensitive data without exposing either the data or the model to the host system or service provider.
- Secure Model Training: Protect training data and emerging model parameters during the training process, preventing data poisoning or model extraction attacks.
- Trustless AI Marketplaces: Enable secure sharing and monetization of AI models without risking intellectual property theft.
- Verifiable AI Results: Provide cryptographic proof that AI outputs were generated by specific models running in secure environments, enhancing trust in critical applications.
- Regulatory Compliance: Meet stringent data protection requirements by ensuring data remains encrypted throughout the AI pipeline.
- Autonomous AI Agents: Enable AI agents to securely manage cryptographic keys and digital assets without exposing sensitive credentials.
Case Studies
TEE in Agent Frameworks
| 🤖 Eliza: Secure AI Agent Framework with TEE Integration | tee_eliza.png | Eliza TEE Plugin |
| 🎮 Virtuals: Game Agents Running in Secure TEE Environment | tee_game_agents.png | Virtuals Game Agent |
Other TEE-AI Integrations
| 📡 Vana Network: Decentralized Data Privacy with TEE | tee_vana.png | Phala x Vana |
| 🌐 0G: Confidential AI Computing in Decentralized Networks | tee_0g.png | Phala x 0G |
| 💰 Fairblock: Unruggable AI with MPC-TEE Hybrid Architecture | tee_fairblock.png | Phala x Fairblock |
| 🌱 Spore.fun: Autonomous AI Evolution in Secure Environments | tee_spore.png | Spore.fun |

