Successful Cases
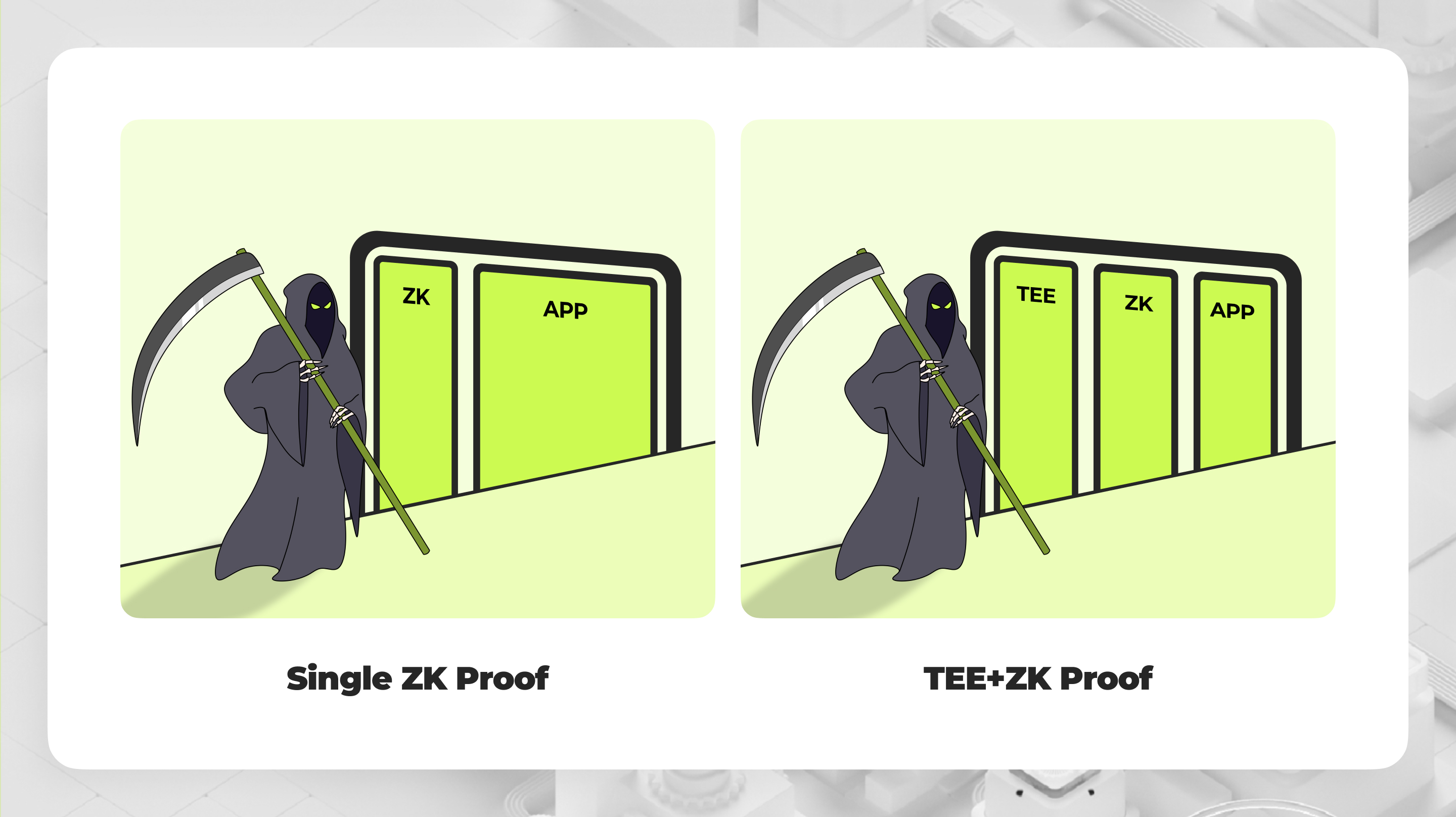
Multi-Proof ZK and TEE
Integrate Zero-Knowledge proofs with TEE for verifiable private computing.
Introduction

- No single cryptographic system can be guaranteed to be 100% secure. For instance, zero-knowledge proofs (zk) can have soundness bugs that are difficult to detect, while Multi-Party Computation (MPC) is susceptible to collusion risks between nodes.
- Privacy in zkRollups cannot be fully guaranteed because sequencers can extract user transaction data during proof generation.
- Verifiability in Fully Homomorphic Encryption (FHE) computations is challenging because the FHE server may not perform computations correctly, and without knowing the correct result, we cannot verify its accuracy.
The Need for Multi-Proof Systems
In the blockchain space, our vision is to bring privacy, security, and verifiability to users. Our ultimate goal is to design a system that can simultaneously fulfill these attributes. However, relying on a single proof system to achieve this is impractical for several reasons:- No single cryptographic system can be guaranteed to be 100% secure. For instance, zero-knowledge proofs (zk) can have soundness bugs that are difficult to detect, while Multi-Party Computation (MPC) is susceptible to collusion risks between nodes.
- Privacy in zkRollups cannot be fully guaranteed because sequencers can extract user transaction data during proof generation.
- Verifiability in Fully Homomorphic Encryption (FHE) computations is challenging because the FHE server may not perform computations correctly, and without knowing the correct result, we cannot verify its accuracy.
- Hardware-grade safety: The privacy, confidentiality, and data integrity is guaranteed by hardware secure enclave.
- No computation overhead: Applications run TEE have nearly same speed compare with running in normal CPU env
- Low verification cost: The Gas consumption to verify TEE proof is minimal, requiring just an ECDSA verification.
- No Privacy Leak: The execution of ZK Prover running in TEE can be verified that it generates proofs without leaking any user data.
Case Studies
| 🚀Phala Network: Run zk-Rollup STF (state transition function) in TEE | Use-Cases-Multi-Proof.png | Phala SGXProver |
| 🔒Primus: Build Trustless zkTLS with TEE | tee_zktls.png | Primus zkTLS |
| 💾Running SP1 zkVM in TEE H200 with Low Overhead | zkvm-sp1-in-gpu-tee.jpg | SP1 zkVM in TEE |

